01. A Dell PowerScale administrator wants to enable quota notifications for their LDAP users. However, the users' email IDs are not updated in the LDAP environment. What needs to be configured?
a) Local users and groups
b) Local provider
c) Mapping rule
d) File provider
02. What is the correct sequence of phases taken in a full deduplication job?
a) 1. Index updating
2. Duplicate detection
3. Block sharing
4. Sampling
b) 1. Block sharing
2. Duplicate detection
3. Index updating
4. Sampling
c) 1. Duplicate detection
2. Sampling
3. Block sharing
4. Index updating
d) 1. Sampling
2. Duplicate detection
3. Block sharing
4. Index updating
03. Refer to the exhibit. What is the actual protection level of the FEATURE.wmv file?

a) N+2n
b) N+1
c) N+2d:1n
d) N+2
04. When preparing a PowerScale cluster for SyncIQ disaster recovery, what must be configured first?
a) Network routing and firewall settings for CloudPools
b) SmartQuotas and file pool policies
c) Cluster-to-cluster replication policies and root directories
d) Only SnapshotIQ policies for the source cluster
05. A Dell PowerScale administrator has four H600 nodes and eight A2000 nodes in the cluster. The file pool policy is configured to have all new data written to the H600 nodes. After a few weeks, the administrator has some concerns about the available capacity on the H600 nodes.
Which feature should be configured to accept writes, even after the H600 nodes become full?
a) VHS
b) Spillover
c) SmartPools
d) GNA
06. What is a reason why Dell PowerScale NAS solutions work effectively with Big Data workflows?
a) Provide a scale-up solution
b) Function as single block-based storage
c) Provide multiple aggregates of volumes
d) Function as a single repository of data
07. A company plans to build two Dell PowerScale clusters in an active-active disaster recovery environment. The initial requirement is to have one access zone for their finance department. Which recommended directory structure meets the requirement?
a) Cluster_A:
/ifs/finance
/ifs/finance
Cluster_B:
/ifs/finance
/ifs/finance
b) Cluster_A:
/ifs/cluster_a/finance
/ifs/cluster_b/finance
Cluster_B:
/ifs/cluster_a/finance
/ifs/cluster_b/finance
c) Cluster_A:
/ifs/cluster_a
/ifs/cluster_b
Cluster_B:
/ifs/cluster_a
/ifs/cluster_b
d) Cluster_A:
/ifs/finance/cluster_a
/ifs/finance/cluster_b
Cluster_B:
/ifs/finance/cluster_a
/ifs/finance/cluster_b
08. What is the order of precedence for NFS export policies?
a) 1. Root clients
2. Always RW clients
3. Clients
4. Always RO clients
b) 1. Always RW clients
2. Always RO clients
3. Root clients
4. Clients
c) 1. Clients
2. Always RO clients
3. Always RW clients
4. Root clients
d) 1. Always RO clients
2. Root clients
3. Clients
4. Always RW clients
09. A financial services company must ensure that client data cannot be altered or deleted once written, for at least seven years, to meet regulatory compliance. They also want to ensure storage reporting for each business unit and be prepared for disaster recovery replication.
Which configuration best addresses these requirements?
a) Enable SmartQuotas only, because quotas inherently prevent data deletion
b) Use SnapshotIQ for immutable copies, set soft quotas only, and rely on CloudPools for replication
c) Configure SmartDedupe to prevent file modification and SyncIQ for replication
d) Implement SmartQuotas for usage tracking, SmartLock Enterprise for WORM retention, and configure SyncIQ for replication
10. Refer to the exhibit. Which port is used to attach the node to the internal network?
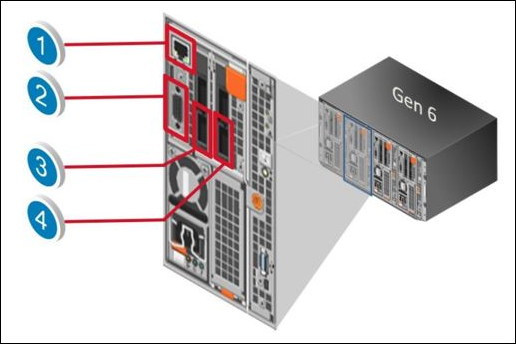
a) 1
b) 2
c) 3
d) 4
 The purpose of this Sample Question Set is to provide you with information about the Dell Technologies PowerScale Deploy 2023 exam. These sample questions will make you very familiar with both the type and the difficulty level of the questions on the D-PSC-DY-23 certification test. To get familiar with real exam environment, we suggest you try our Sample Dell Technologies PowerScale Deploy Certification Practice Exam. This sample practice exam gives you the feeling of reality and is a clue to the questions asked in the actual Dell Technologies Certified PowerScale Deploy 2023 certification exam.
The purpose of this Sample Question Set is to provide you with information about the Dell Technologies PowerScale Deploy 2023 exam. These sample questions will make you very familiar with both the type and the difficulty level of the questions on the D-PSC-DY-23 certification test. To get familiar with real exam environment, we suggest you try our Sample Dell Technologies PowerScale Deploy Certification Practice Exam. This sample practice exam gives you the feeling of reality and is a clue to the questions asked in the actual Dell Technologies Certified PowerScale Deploy 2023 certification exam.

