 The purpose of this Sample Question Set is to provide you with information about the EC-Council Application Security Engineer - Java exam. These sample questions will make you very familiar with both the type and the difficulty level of the questions on the 312-96 certification test. To get familiar with real exam environment, we suggest you try our Sample EC-Council CASE Java Certification Practice Exam. This sample practice exam gives you the feeling of reality and is a clue to the questions asked in the actual EC-Council Certified Application Security Engineer (CASE) - Java certification exam.
The purpose of this Sample Question Set is to provide you with information about the EC-Council Application Security Engineer - Java exam. These sample questions will make you very familiar with both the type and the difficulty level of the questions on the 312-96 certification test. To get familiar with real exam environment, we suggest you try our Sample EC-Council CASE Java Certification Practice Exam. This sample practice exam gives you the feeling of reality and is a clue to the questions asked in the actual EC-Council Certified Application Security Engineer (CASE) - Java certification exam.
These sample questions are simple and basic questions that represent likeness to the real EC-Council 312-96 exam questions. To assess your readiness and performance with real time scenario based questions, we suggest you prepare with our Premium EC-Council CASE Java Certification Practice Exam. When you solve real time scenario based questions practically, you come across many difficulties that give you an opportunity to improve.
EC-Council 312-96 Sample Questions:
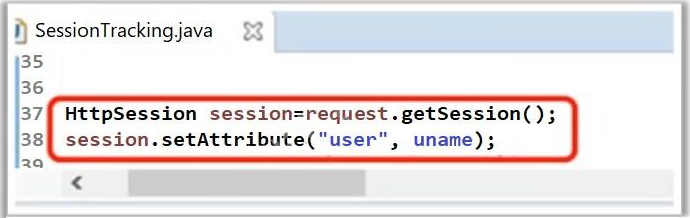
a) Data flow diagram
b) public boolean validateUserName() {String CategoryId= request.getParameter('CatId');}
c) ex.getError();
Answers:
|
Question: 01 Answer: c |
Question: 02 Answer: a |
Question: 03 Answer: b |
Question: 04 Answer: a |
Question: 05 Answer: b |
|
Question: 06 Answer: a |
Question: 07 Answer: d |
Question: 08 Answer: c |
Question: 09 Answer: d |
Question: 10 Answer: c |
Note: For any error in EC-Council Certified Application Security Engineer (CASE) - Java (312-96) certification exam sample questions, please update us by writing an email on feedback@edusum.com.
